First, you need to order a server. I use KVM-based root servers from Netcup, but you can choose any provider that offers similar specs.
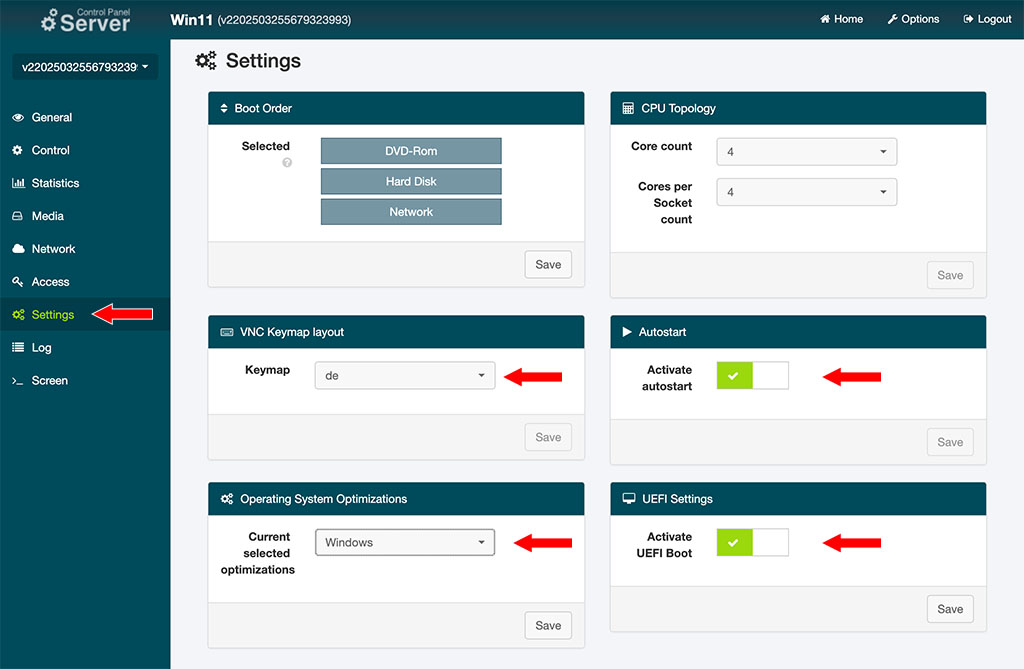
Windows 11 requires UEFI, Secure Boot, and TPM 2.0 – requirements that many virtual servers (VPS, Virtual Private Servers) do not meet. Even on a root server with KVM virtualization (Kernel-based Virtual Machine), TPM and Secure Boot are usually not available, so a registry hack is necessary to enable the installation. Additionally, Windows 11 requires at least 2 CPU cores, 4 GB of RAM, and 64 GB of storage. A KVM-based root server provides the necessary flexibility for ISO booting, stable performance, and full control over resources.
For using a server as a Windows PC, a plan with 4 dedicated cores, 8 GB of DDR5 RAM, and a 256 GB NVMe SSD should be sufficient.
(more…)